By Lee Rickwood
New tech gadgets, mobile devices and online networks are facing increased risks, but some of the biggest cyber threats are the oldest.
In the case of PC malware and online vulnerabilities, the old SQL Slammer worm (which first came to light back in 2003) is still the most common source of malicious Internet traffic today.

IBM's X Force says we need to be ahead of a growing online threat.
Even so, criminal gangs and criminally minded individuals are becoming smarter, more ambitious and more sophisticated with tech attacks on computers at home and at work.
What’s more, they’re after a fresh and growing target – mobile devices and cloud-based computing services.
Altogether, vulnerability disclosures increased a whopping 27 per cent last year – reaching the highest level in history, according to the X-Force 2010 Trend and Risk Report, released by International Business Machines Corp.
Those are just the “disclosed” attacks – many are never reported, out of embarrassment or potential liability.
What’s worse, IBM’s X-Force report says, many Web exploits are publicly released months after the public disclosure of the vulnerabilities they target, suggesting that attackers are able to use exploit and re-cycle code, even after patches have been made available.
There were more than 150,000 security events per second per day last year! More than enough to build a solid and somewhat sobering report. From its nine global Security Operations Centers (SOC), the IBM X Force team sends out global Web crawlers and international spam collectors that help the real-time monitoring of 13 billion security events every day, on behalf of nearly 4,000 clients in more than 130 countries.
The team determined that close to half of vulnerability disclosures in 2010 were Web application flaws, mostly resulting from cross-site scripting and SQL injections.
Those two methods were also cited by IBM in 2009 as the most popular for exploiting Web application flaws, so you’d be forgiven if you wonder why more tangible and robust remedies have not been developed and deployed.
In fact, even in 2007, Symantec was reporting that cross-site scripting was being used by like 80 per cent of attackers to bypass normal website access controls by injecting their own client-side scripts (including fake content, user instructions and data capture fields) into otherwise normal Web pages.
“These [web application] vulnerabilities represent just the tip of the iceberg since many organizations develop third-party applications in-house that are not subject to public vulnerability reports,” the report cited as one possible reason.
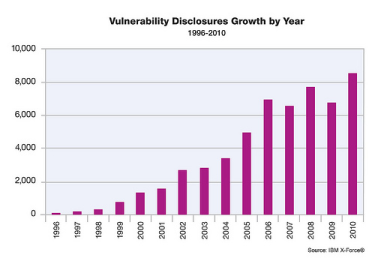 The report also noted that security has become a primary concern of companies in adopting emerging technologies, such as cloud computing and mobile devices. X-Force data shows a rise in vulnerability disclosures and exploits that specifically target such new environments.
The report also noted that security has become a primary concern of companies in adopting emerging technologies, such as cloud computing and mobile devices. X-Force data shows a rise in vulnerability disclosures and exploits that specifically target such new environments.
There is a reported decline in phishing attacks and spam blankets, which is a good sign, but those risks are being replaced by more sophisticated attacks like the so-called ‘Advanced Persistent Threat’ after high profile attacks on major corporate enterprises by sophisticated, targeted attackers.
“From Suxnet to Zeus Botnet, a widening variety of attack methodologies is popping up each day,” Tom Cross, the threat intelligence manager for IBM X-Force, described. “The numerous, high profile targeted attacks in 2010 shed light on a crop of highly sophisticated cyber criminals, who may be well-funded and operating with knowledge of security vulnerabilities that no one else has. Staying ahead of these growing threats and designing software and services that are secure from the start has never been more critical.”
So what can we do? How do tech users stay ahead of the curve and protected their devices and their data?
Cyber safety education and awareness is one step, for home users, small business operators and corporate IT departments alike, organizations like IBM constantly underscore. They recommend that you keep up-to-date through security news bulletins and online threat alerts, many of which the company provides to clients and the general public.
Among the cyber safety tips for home users:
Installing, activating and updating security software is a must. Use anti-virus, anti-spyware software and install a firewall.
- Turn on or activate auto updates.
- Use strong passwords, and change them often.
- Be wary of e-mails (and especially attachments) from people you do not know.
- Don’t give out personal or financial information through e-mail.
- Make sure you wipe your computer clean before selling or trading or disposing of it.
Some mobile safety tips:
- Be sure your handset’s security settings are turned on, and set properly. Set and use a strong password. Check for security software tools for the mobile operating system you use.
- Encrypt your data whenever possible, and back it up regularly
- Make sure you delete all personal information on your phone before recycling or trading it in for a new one.
- Put a PIN on your phone and a different one on your SIM card if possible. Don’t rely on default factory settings.
- Check your handsets IEME number – there should be a unique International Mobile Equipment Number on your phone (try keying in *#06#). You can use it to tell your network provider to stop service, if your phone is lost or stolen. And report it immediately if it is.
Business Safety Tips
- Install security software and auto update features for anti-virus, anti-spyware and firewall protection. Spam filters should always be in place, as should a good understanding of how to deal with suspicious emails should they get through (and they will).
- Have a company-wide data protection, retention and back-up strategy. And a company-wide IT usage policy for employees.
- If the company does not have a full-time IT manager, assign someone to have responsibility over the basics like passwords, back-ups and software updates.
Companies large and small should develop a culture of security. Internet and tech safety should be second nature nowadays, not a special or temporary commitment.
Online security is a bottom-up and a top-down activity, needing the commitment of all staff and the support of all available resources.
# # #
To see the IBM X-Force Trend and Risk Report (it has more than 128 pages), visit: https://www-03.ibm.com/security/landscape.html.
For more information on IBM Security Solutions, visit: www.ibm.com/security .
To learn more about the IBM Institute for Advanced Security, visit: https://www.instituteforadvancedsecurity.com/.
- More coverage of security
- More coverage of privacy
- More coverage of security