By Gadjo Cardenas Sevilla
Since smartphones are quickly replacing PCs as the personal communication device of choice, the need to secure our mobile devices has become critical.
Far easier to lose and more tempting to steal, smartphones have become crucial components of our lives not just because they keep us connected but because of the wealth of personal information they contain.
 Forget the apps and games, we fill our devices with financial information, personal photos, work contacts and thousands of bits of information that can be exploited by thieves, hackers and other criminals.
Forget the apps and games, we fill our devices with financial information, personal photos, work contacts and thousands of bits of information that can be exploited by thieves, hackers and other criminals.
With the advent of mobile payments around the corner and the possibility that the smartphones we use can become our digital wallets, this becomes an even bigger concern.
Not to mention that for some reason, smartphones bought off contract sell for anywhere between $400-$900 depending on the model, more expensive than tablets and even more expensive than many notebook and desktop PCs.
Smartphone security is at least a two step process. The first is making sure that no one can access your smartphone and this can be done easily by locking the device with an alphanumeric password or in some cases a series of gestures. Newer smartphones even include a fingerprint reader or in the case of the Galaxy Nexus, a face unlock feature that reads facial details. These are more gimmicky than useful, users should always lock their smartphones with a passcode.
In the event that the phone still gets stolen or lost and cannot be retrieved, there needs to be a way to remote-wipe the device or even render it useless to the thieves. This is the second and more critical step.
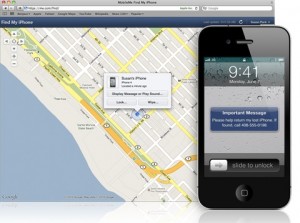
Apple’s iOS offers a Find My iPhone feature that can seek out registered iPhones and track them on a map, this feature also allows the sending of text messages or alert sounds to notify nearby persons that a missing phone is around.
When all fails, there is the option to remotely wipe out all the data in the smartphone. Users who set up iCloud can later on download previously saved information on to a new device if necessary
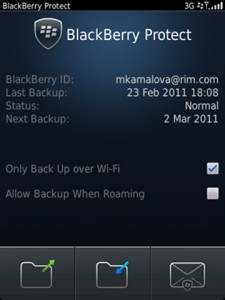
BlackBerry’s Protect service offers a similar service, although RIM’s added benefit is that a lot of the data specially messages are resident on their servers so they can be restored or even accessed remotely.
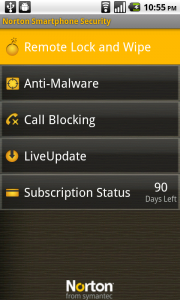
Some Google Android devices can use Google Sync to backup and even remote wipe and we know that Motorola’s Motoblur had this feature from the very start. Norton’s Smartphone Security suite for Android doesn’t just enable remote locking and wiping but also deals with the growing malware and virus problem that’s emerged to meet the fastest rising Mobile OS.
The responsibility ultimately falls on us, the users. We need to secure our devices by keeping them close and using passwords, make regular backups of our device and enable them to be found if lost or wiped remotely to protect the most important personal information.



