A new report from the University of Toronto’s Citizen Lab says a major cyber-espionage campaign has hundreds of targets around the world.
The campaign has “a strong Russian nexus” and it uses techniques that single out consumer gadgets and digital devices, including iPhones.
Cyber-hackers often aim at government, military and political targets, but the Citizen Lab report says our wider civil society is also in the cross-hairs. The targets include journalists, academics, lawyers, human rights researchers and cyber-investigators.
As a result, says Ronald Deibert, the Director at Citizen Lab, “[W]e have to start thinking broadly as citizens of this planet … how we engage in stewardship over cyberspace collectively.” In discussing Citizen Lab activities with Democracy Now! host Amy Goodman, Deibert said of the challenge civil society faces: “Unfortunately, it’s an uphill battle, and it’s getting steeper.”

Ron Deibert, (OOnt, PhD, University of British Columbia) is Professor of Political Science, and Director of the Citizen Lab at the Munk School of Global Affairs, University of Toronto.
In its report, titled Tainted Leaks: Disinformation and Phishing with a Russian Nexus, Citizen Lab clearly states that the cyber-espionage campaign targets people from at least 39 countries and international organizations.
The campaign uses sophisticated phishing techniques as well as the planting of disinformation in leaked stolen materials, designed to achieve a propaganda end or disrupt human rights campaigns and social justice activities.
Phishing campaigns try to trick a user into entering personal credentials into a carefully disguised form or fake application. Emails have personal or emotional subject lines, or even promises of important information about personal online security, to draw a victim in. They also try to get recipients to click on an otherwise innocent-looking link which leads to a file that then infects or otherwise compromises their device, making it controllable by unknown third parties.
Citizen Lab, based at the University of Toronto’s Munk School of Global Affairs, has been working for many years to expose cyber-espionage campaigns, find major security flaws in digital devices, and identify the myriad of threats emerging from the intersection of Big Data and Big Brother. Its experience in uncovering global cyber-espionage campaigns dates back to 2009’s Tracking Ghostnet report.
Deibert says civil society worldwide is now facing an epidemic of targeted digital espionage, yet little information about it comes into the public domain, partly he says due to government inaction or unwillingness, but also due in part to the existence of private sector proprietary products that represent significant commercial value when used by paying clients.
Software hacking tools are a hot commodity: if you can’t write the code yourself, you can buy off-the-shelf tools to invade pretty much anything.
A million dollars will get you every keystroke, sound, message and GPS location reading possible from multiple iPhone users once you buy the software that’s available out there. (Remember the iPhone/FBI case involving the San Bernadino terrorists? The FBI wanted Apple to provide a back door hack, but without that company’s cooperation, the agency then went “rogue” and bought some software for itself.)
Citizen Lab has previously investigated and reported on how similar software, developed by an Israeli company, was used by the Mexican government to target a groups of international investigators digging into human rights violations in Mexico, for example.
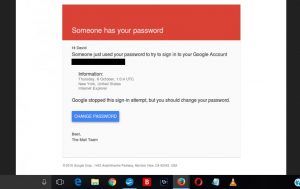
Phishing campaigns try to trick a user into entering personal credentials into a false form or fake application. Emails that use personal or emotional subject lines, or even promise important information about your online security, try to get recipients to click on a link that then infects or otherwise compromises their device.
In analyzing the technical details associated with the Russia-aligned campaign and its identifiable modus operandi, the Citizen Lab research team illustrated how the twin strategies of phishing and tainted leaks can be used to penetrate civil society targets, and to sow mistrust and disinformation, say, during an election campaign or national referendum.
“Tainted leaks plant fakes in a forest of facts in an attempt to make them credible by association with genuine, stolen documents,” noted senior researcher John Scott-Railton.
The Citizen Lab researchers have not conclusively linked the identified cyber-campaign with a particular Russian government entity, but they say many elements of the campaign overlap with groups previously identified as Russia-affiliated by other reports. This overlap includes operations associated with the successful breach in 2016 of the email account of John Podesta, the former chairman of the 2016 Hillary Clinton presidential campaign.
In one way or another, that breach influenced the Presidential election.
“There’s no doubt in my mind that actors affiliated with the Russian government tried to influence the U.S. election process,” Deibert stated confidently. “They are the ones that were responsible for breaching the computer systems of the DNC, John Podesta’s emails, as well as many other groups that we identified in our report, groups and individuals.”
Looking beyond cyber-crime for profit, although that is clearly still a good motivator, we are seeing how the Internet is being controlled and manipulated by governments in order to censor, monitor, and influence their citizens, thanks to the work done at Citizen Lab.
-30-



