The fact that a legitimate piece of software can be used to control if not extract the contents of someone else’s smartphone – without permission – is a window into the ever-growing and ever-capable commercial spyware market.
The fact that one particular piece of such software has been used so widely around the globe is a warning that the marketplace is unmonitored, perhaps corrupt, and surely in need of independent regulation.
Known as Pegasus and developed by an Israeli company called NSO Group, the software sold to and used by many governments and state agencies can intercept and collect all sorts of personal, private data (messages, calls, emails, photos, and locations) without permission – even without the awareness – of the target victim.
Even a device’s microphone and its camera can be remotely triggered and monitored in real-time using commercial spyware.
Reports about the alleged use of the Israeli software have been researched and published by more than a dozen international media organizations (including the research and technical investigations done here in Canada, at The Citizen Lab in Toronto).
Reports ended up citing dozens of possible Pegasus clients in more than 45 countries and 50,000 phone numbers on a list of potential target devices.
But many of those reports did not mention a large number of other commercially available spyware programs and the established existence, if not exponential growth, of what’s been called “the private surveillance industry”.
Encompassing not only Israel, of course, but many other jurisdictions, the commercial spyware industry embraces participants from several other countries, among them France, China, the United States, Italy, and yes, Canada.

Spyware products allow an unknown remote agent to control every aspect of your phone – without you knowing it, and without you doing anything! (Photo: Blogtrepreneur Flickr/howtostartablogonline.net)
The international spyware industry has developed many effective, efficient eavesdropping tools with capabilities to turn your smartphone into someone else’s. Spyware products allow an unknown remote agent to control every aspect of your smartphone’s features and functions – without you knowing it, and without you doing anything!
That’s not only plenty of reason for device owners and users to worry: the growth of the commercial spyware industry has several big tech makers worried, too.
With co-signers like Cisco, VMWare, Google, Facebook and more, Microsoft is part of a legal action against the NSO Group. In a company blog post, Microsoft charges that spyware makers “threaten human rights whether they seek to or not” and they conduct their “dangerous business without legal rules, responsibilities or repercussions.” Microsoft continues to warn against what it calls a “world where private sector companies manufacture and sell cyberweapons”, calling the development “dangerous for consumers, businesses of all sizes and governments.” The tech giant continues to work with Citizen Lab, which has long worked to identify cyber threats worldwide.
With smartphone users now showing some concern and device-makers now taking some action, analyst David Kaye’s report on “the private surveillance industry” has become a predictive and foundational document.
Kaye is the Special Rapporteur on the promotion and protection of the right to freedom of opinion and expression for the United Nations.
More than two years ago, he described the private surveillance industry as a “free-for-all, an environment in which States and industry are collaborating in the spread of technology that is causing immediate and regular harm (italics added) to individuals and organizations that are essential to democratic life – journalists, activists, opposition figures, lawyers and others.”
In a more recent report, Steven Feldstein listed many of the specific vendors and spyware products in the Mendeley Data Commercial Spyware Global Inventory, V2, 2020.
His listing of the commercial spyware products procured and used by governments around the world raises the question of whether the industry products or government actions (or perhaps both) he has cited violate “principles of legality, necessity, proportionality, and legitimacy”?
From NSO Group and Pegasus to Black Cube, Cellebrite, FinFisher, Blue Coat, Nexa Technologies, Hacking Team/Memento, CyberPoint, L3 Technologies, and Verint, among others, a growing number of digital surveillance tools on the market have very similar, very powerful capabilities.
KRAIT, for example, from the Italian developer Hacking Team (now known as Memento), is an Android equivalent of the Pegasus iPhone-centric tool (although these tools are often multi-platform).
Like Pegasus, KRAIT can be used to take over a target device with no action needed by the device owner. The mobile device’s location data, call logs, address book, and text messages are accessible to the KRAIT controller. Encrypted communications, such as those shared on messaging apps like Signal, Telegram, and WhatsApp can be intercepted, read, and stored.
But perhaps even more worrying is the fact generic components of a safe, secure and functioning Internet can be used as surveillance tools.
That’s the difficult spot a Canadian company called Sandvine seemed to find itself in when reports surfaced that its software tools were being used by repressive governments around the world.
Researchers at the digital rights group Qurium Media Foundation were among those who said Sandvine’s telecom tools were being used by the Egyptian (and other) governments to block people’s access to hundreds of websites, including news and media sites.
Sandvine said its technology was “not intended to thwart human rights or block the broad, free flow of information’’ just the opposite, in fact: “[I]t is designed to … ensure that citizens have high quality and better access to information worldwide.’’ The Canadian company says it no longer works with certain identified regimes.
(For its part, NSO has released a transparency report and published excerpts from its contracts with customers indicating that its products be used only for criminal and national security investigations.)
In order to be safe from unlawful surveillance, we need to be able to trust such statements. We need to be able to trust our devices. We need to be able to trust the marketplace and our government.
That is why Kaye and many others are advocating for the creation of open and transparent public mechanisms for the approval, licensing, and oversight of commercial spyware and surveillance technologies.
Some are calling for a moratorium on its sale and transfer entirely; others say a mechanism for restitution for victims is needed as well.
Eitay Mack, a human rights lawyer and activist based in Israel, has filed petitions to revoke export licenses of certain technology companies in his country and issued calls to implement a more comprehensive review process before surveillance technologies can be sold to a new customer.
As Kaye writes in his report, “It is time” for strict supervision of the industry “with the goal of protecting human rights for all.”
The fact that “human rights for all” needs to be put in place as a goal of the marketplace, and is not already its core operating criteria, is a condemnation of not just the marketplace, but of its regulators and participants.
# # #
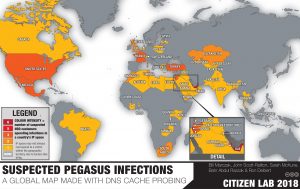
Researchers at Citizen Lab in Toronto are among those describing how commercially available spyware like Pegasus is being used worldwide. Citizen Lab says the usage is “part of a broader industry-wide shift towards more sophisticated, less detectable means of surveillance.”
-30-




Apple has released a software fix to block a method of infecting its mobile and computing devices with the Pegasus spyware. Apple lists the fix as CVE-2021-30860, describing the spyware injection method as a zero-click exploit that could lead to arbitrary code execution. Toronto-based Citizen Lab discovered the exploit, called FORCEDENTRY, and notified Apple. According to Citizen Lab, FORCEDENTRY has been in use since at least February 2021.
https://support.apple.com/en-us/HT212807
Four days after this story was posted, U.N. human rights experts called for a global moratorium on the sale and transfer of surveillance technology until robust regulations that guarantee its use in compliance with international human rights standards are in place.
https://apnews.com/article/technology-united-nations-spyware-e1bfa1f8242f39da856fc0a8bf2793aa